
Cybersecurity organizations Access Now and Citizen Lab have released a report on a large-scale phishing attack that targeted human rights organizations in Russia, Belarus, and Ukraine, international NGOs active in Eastern Europe, independent media outlets, and a former U.S. ambassador. The report analyzes two waves of attacks: one in 2022-2023 and another in 2024.
The latest campaign, which took place in 2024 and was dubbed “COLDRIVER,” has been linked to the Russian hacker unit Callisto Group (also known as Dancing Salome, SEABORGIUM, STAR BLIZZARD, and TA446), which is believed to be under the control of the FSB Information Security Center. This group is known for carrying out cyberattacks against military and government institutions, think tanks, and journalists in Western countries. A similar campaign, named COLDWASTREL, was conducted in 2022-2023, according to Access Now and Citizen Lab.
How the FSB cyberattacks were carried out
The most common attack method in the first wave (2022-2023) involved sending phishing emails, either from hacked accounts or from addresses that looked almost identical to real ones, often with just one letter changed to make the forgery hard to spot. The Insider uncovered this campaign in October 2022 and alerted various cybersecurity organizations. These phishing attacks were highly personalized, with the email topics closely related to the recipient's daily work, often referring to upcoming events or seemingly relevant financial matters. The emails typically included “blocked” PDF attachments along with a link to unblock them. Clicking the link would open a fake Proton email login page, prompting the victim to enter their login credentials. If they did, the attackers would gain access to their information.
In December 2024, the U.S. and UK brought charges against two Russian citizens involved with the Callisto Group. The indictment states that the hacker group breached computers in the U.S. and allied countries, stealing information that was later used in operations aimed at exerting malicious foreign influence, particularly to impact the 2019 UK elections. The UK has also filed charges.
The charges are against Ruslan Aleksandrovich Peretyatko, an officer of the Information Security Center (“Center 18”), and Andrey Stanislavovich Korinets. According to The Insider, employees of the Radio-Electronic Intelligence Center, known as the “Center 16” (Military Unit No. 71330), were also involved in the hacking campaign.
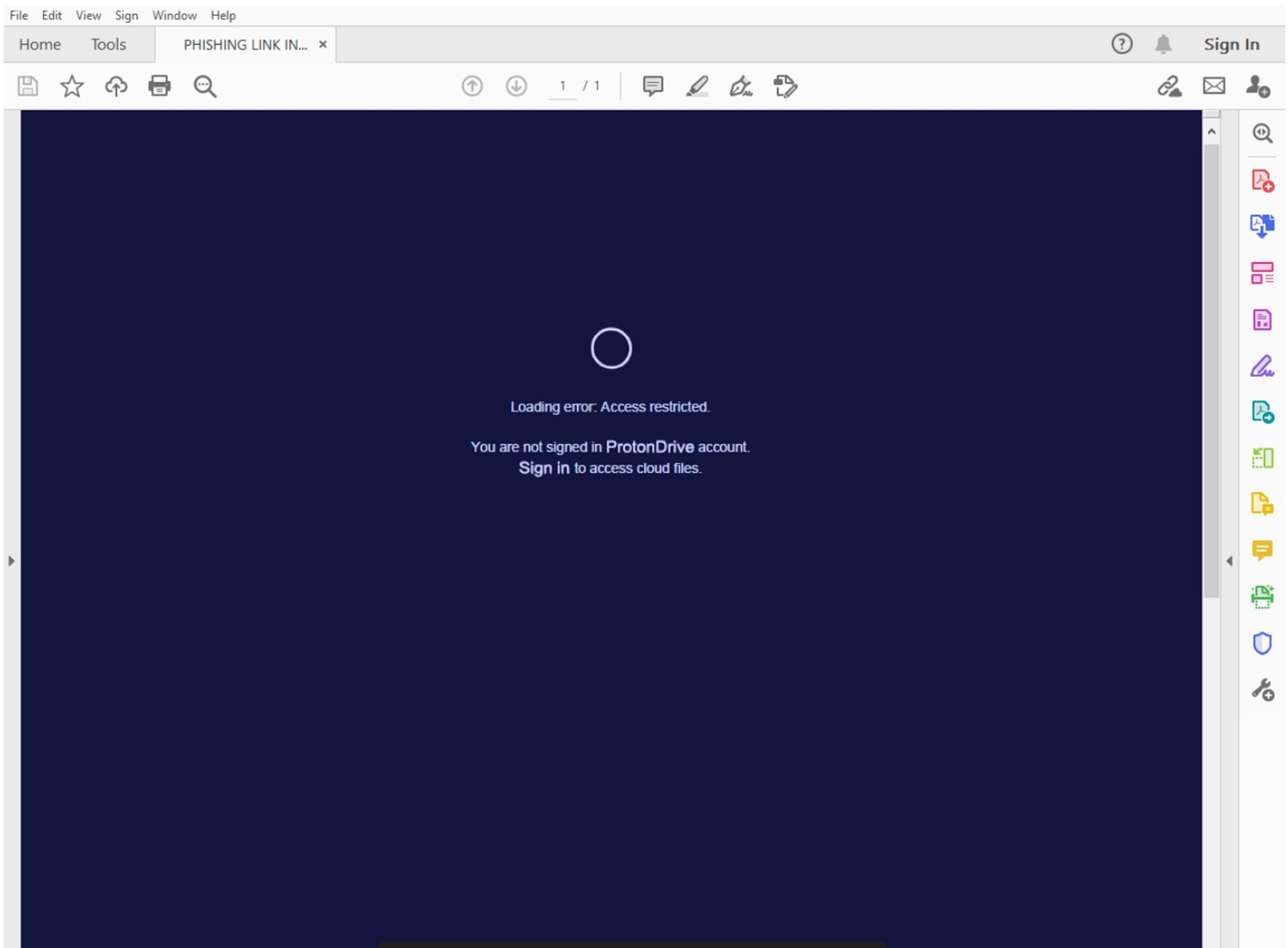
Sample of a PDF preview presented to targets as part of the COLDWASTREL campaign
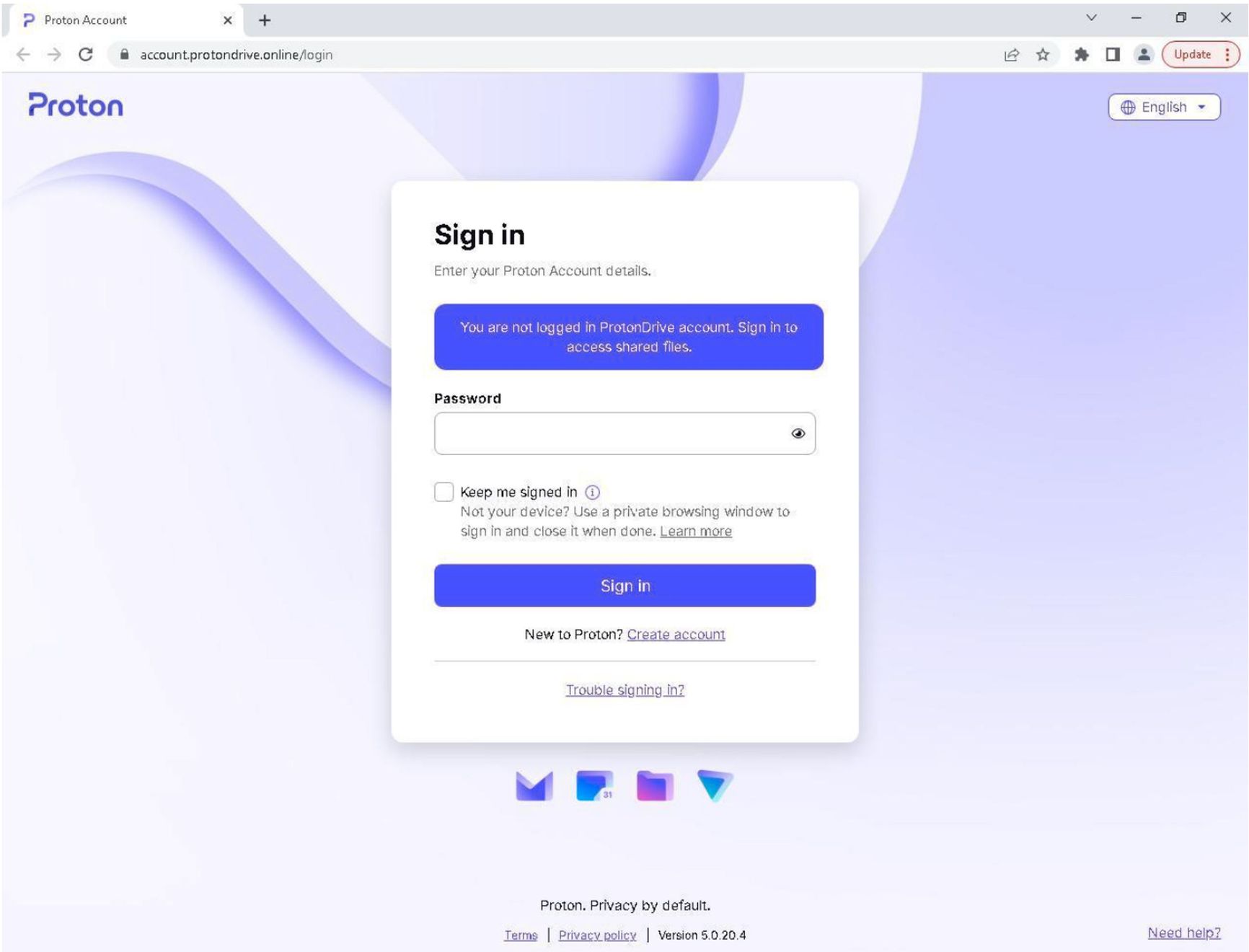
Sample of fake Proton Mail login page presented to targets as part of COLDWASTREL campaign
In later attacks, the hackers employed a different tactic: they set up a mail server with fake domains to impersonate legitimate organizations, targeting actual partners and colleagues of those organizations. This approach was often paired with the use of slightly altered email addresses. The discovery of these servers allowed Access Now to warn potential victims. At least one international human rights organization confirmed that it had fallen victim to such an attack.
In 2023, the Russian human rights organization First Department informed Access Now and Citizen Lab about a phishing email that several international NGOs had received. The sender pretended to be an employee using the Proton Mail platform. This same employee had previously lost access to their Proton Mail account after falling victim to a phishing attack in October 2022 — this is how the recipients realized the email was not authentic.
During the investigation, analysts found that the attacker's IP address was linked to domains that mimicked well-known NGOs. They alerted the affected organizations, and one of them confirmed receiving a similar phishing email.
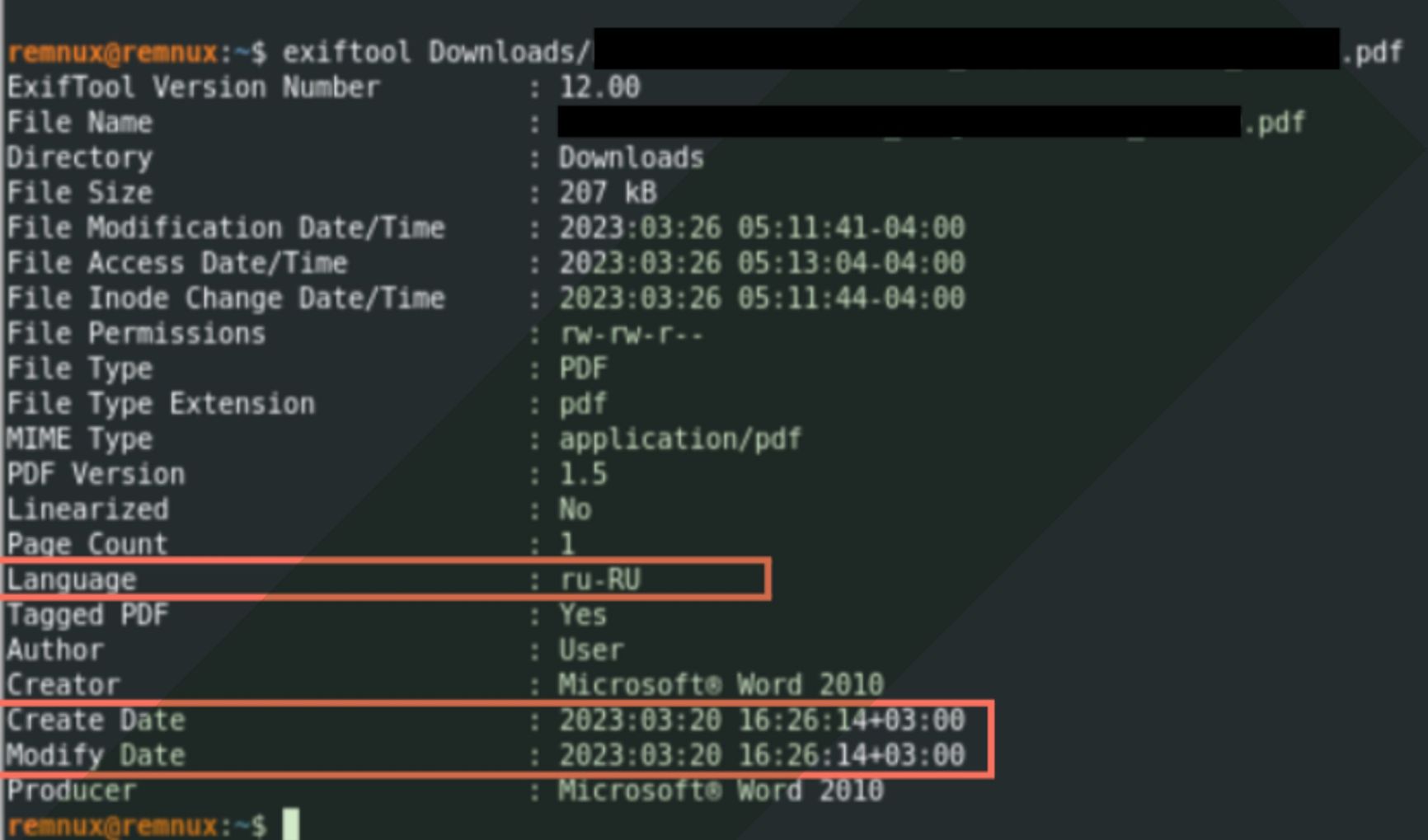
The targets of these attacks were involved in human rights work in Russia and Ukraine. The attackers used content directly related to the victims' work, such as funding and grant proposals. An analysis of the EXIF data in PDF documents revealed that the documents were created in the GMT+3 time zone (Moscow time), and the language settings were set to ru-RU (Russian).
In December 2024, the U.S. and UK brought charges against two Russian citizens involved with the Callisto Group. The indictment states that the hacker group breached computers in the U.S. and allied countries, stealing information that was later used in operations aimed at exerting malicious foreign influence, particularly to impact the 2019 UK elections. The UK has also filed charges.
The charges are against Ruslan Aleksandrovich Peretyatko, an officer of the Information Security Center (“Center 18”), and Andrey Stanislavovich Korinets. According to The Insider, employees of the Radio-Electronic Intelligence Center, known as the “Center 16” (Military Unit No. 71330), were also involved in the hacking campaign.
The next phishing campaign occurred in 2024, targeting Russian and Belarusian organizations, international NGOs working in Eastern Europe, independent media outlets, and a former U.S. ambassador. Once again, the attackers sent emails with “blocked” PDF files, supposedly from people the victims knew. However, this time, instead of using fake domains, they relied on virtual private servers, primarily hosted by Hostinger International Limited — a major Lithuanian provider ranked among the top five most popular hosts for phishing attacks, according to the Cyber Crime Information Center's 2023 data. Analysts noted that this shift to virtual private servers made it harder to identify the victims.
In December 2024, the U.S. and UK brought charges against two Russian citizens involved with the Callisto Group. The indictment states that the hacker group breached computers in the U.S. and allied countries, stealing information that was later used in operations aimed at exerting malicious foreign influence, particularly to impact the 2019 UK elections. The UK has also filed charges.
The charges are against Ruslan Aleksandrovich Peretyatko, an officer of the Information Security Center (“Center 18”), and Andrey Stanislavovich Korinets. According to The Insider, employees of the Radio-Electronic Intelligence Center, known as the “Center 16” (Military Unit No. 71330), were also involved in the hacking campaign.
Sample of the PDF preview presented to the targets as part of the COLDRIVER campaign
When victims clicked on the link in the email, they were either taken to a fake login page (similar to the 2023 attack) or directed to download malware. PDF files from the 2024 campaign no longer included creation or modification dates. The language was changed to English (en-US), and the “Author” metadata featured Western names. Access Now suggests that the metadata might have been removed to avoid leaving traces that could be used for attribution. However, analysts were still able to link the attack to the Russian FSB, as the strategy closely resembled the work of the Callisto group.
Access Now suspects that the attackers may have gained unauthorized access to some victims' email accounts. The attack could have caused great harm to independent Russian and Belarusian organizations and media, as their email inboxes may contain confidential information about the identity, activities, connections, and whereabouts of employees. The information can be used by Russian authorities as a pretext for assigning “foreign agent” or “undesirable organization” status, which can then lead to criminal prosecution and imprisonment.
How to protect yourself
- Access Now notes that to protect against attacks, it is of primary importance to set up two-factor authentication. However, it's worth remembering that hackers like COLDRIVER may try to trick you into entering the second factor. According to analysts, in the second campaign, the attackers did successfully compromise a victim who had two-factor authentication enabled.
- Users who set SMS messages as a second factor are at risk of having their codes stolen by an attacker who has gained access to their phone account.
- It is recommended to use two-factor authentication options such as security keys or Google Passkeys (for Gmail users). Google and other services offer additional protection services for people who, due to their activities, are at heightened risk of becoming victims of hacking. These services include Google Advanced Protection and Microsoft Account Guard.
In addition, Access Now recommends performing a simple check when receiving suspicious emails:
- Check the sender's email address: have you received messages from this exact account before? COLDRIVER often uses nearly identical email addresses to impersonate senders who are familiar to the target, both personally and professionally. A new email may look like a message from someone you know. Therefore, perform the following checks as well:
- Contact the sender through another communication channel.
- Don't rush to click buttons and links. If you have any concerns or suspicions, do not open the PDF file, and do not follow links in the email. If you are unsure about the safety of a sent document, you can open it directly within the email service: Google, Microsoft, and other companies display file contents directly in the email reader. This feature protects against malicious code embedded in the document, but it does not prevent users from clicking on links. Again: do not click on the links.
- Copy the link into a text editor without clicking on it, and examine it closely. Modern phishing sites are very convincing in mimicking popular services. Often the only giveaway that it’s not a legitimate site is subtle irregularities in the link text.
- See a login page form? Under no circumstances should you enter your data. Consult an expert instead – it's most likely phishing.
- Beware of “encrypted” or “protected” PDF files. Legitimate encrypted PDF files almost never contain “click here” or “Login” buttons inside the PDF. And they do not show a blurred version of the content. If the content is blurred, be extra careful.
If you suspect an attack has occurred, consult a trusted specialist. It's crucial to assess any potential damage to your organization and/or any connected organizations or people. You should also review access logs for your accounts, such as Proton Mail authentication logs, Gmail's latest activity and device access overview, and Microsoft logs for recent login activity.
In December 2024, the U.S. and UK brought charges against two Russian citizens involved with the Callisto Group. The indictment states that the hacker group breached computers in the U.S. and allied countries, stealing information that was later used in operations aimed at exerting malicious foreign influence, particularly to impact the 2019 UK elections. The UK has also filed charges.
The charges are against Ruslan Aleksandrovich Peretyatko, an officer of the Information Security Center (“Center 18”), and Andrey Stanislavovich Korinets. According to The Insider, employees of the Radio-Electronic Intelligence Center, known as the “Center 16” (Military Unit No. 71330), were also involved in the hacking campaign.